The cyber threat to small and medium businesses (SMBs) is more financially damaging than the combined threat of fire, flood, and transport strikes.
While the vast majority of reported cybersecurity breaches over the past 18 months have concerned large and well-known companies across the globe, it is small and medium size businesses that are increasingly in the criminal’s cross-hairs.
by the Ponemon Institute, three in five SMBs have experienced a cyber attack in the last 12 months and one in three believe they are not capable of fending off an attack.

Cybersecurity custome solutions
Custom Solutions
Join our community of cybersecurity thought leaders, practitioners, students, and enthusiasts. Share your thoughts, tips, and tools for information security, cybersecurity, risk management, cybercrime, careers, privacy, etc..
JOINStart Protecting Your Business Against Cyber Attack
Technology is an enabler, giving business the ability to operate faster and more efficiently than ever before. Doing business in this fast paced and complex environment places additional pressure on business and technology leaders to not only learn how to navigate this new landscape but also how to protect themselves in this ever-changing environment. Today’s cyber security landscape is more complex than ever before but, that should’t not stop you from getting stated. Regardless of the size of your business or your technical ability there are some basic steps you can take improve your cyber defenses.
Our Services
Cybersecurity Our services
Information Security Program
Implementing a well-defined and robust security program that is tailored to the specific needs of your business helps to ensure the confidentiality, integrity, availability and privacy of your data and that of your customers. Our advisory services is focused on working with business and technology leaders to develop and implement security programs. Our consultants will develop a comprehensive program and implementation roadmap based on accepted industry best practices and the specific needs of your business.

Our standard approach includes:
- Collecting and analyzing information to understand the goals and objectives of the business, understanding the acceptable risk appetite and tolerance levels of the business.
- Reviewing existing security programs, plans, policies, procedures and controls to determine whether or not security goals and objectives are aligned with those of the business and industry.
- Performing a high-level security assessment to identify the current security posture of the business, high-risk threats and vulnerabilities.
- Working closely with the business and technology leaders to define a security capability maturity level target that is based on the existing capabilities and needs of the business.
- Identifying gaps between the current state capabilities and what is required to achieve the target maturity level.
- Identifying the people, policies, procedures, processes, controls and technologies required to achieve the target maturity level.
- Developing a phased implementation plan and roadmap.
Risk Assessment Services
A critical element in any Information Security Program is how well the organization manages risks. Managing risk involves the identification, assessment, treatment, monitoring and tracking of risk. Since it’s impossible to manage what you don’t know exists, it’s critical to begin any attempt to manage risk by performing a risk assessment to identify, estimate and prioritize the risks to organization’s information assets. To ensure a comprehensive assessment is performed, it’s important to include people, processes and technology in the assessment. Our consultants will develop conduct a Risk Assessment that is tailored to the specific needs of your business and industry.

Our standard approach includes:
- Compiling a list of the information assets of the organization.
- Preforming a business impact analysis to understand the true value of each asset.
- Creating risk scenarios to identify threats and vulnerabilities.
- Combining qualitative and quantitative approaches to estimate the likelihood and potential impact of the risk.
- Providing recommendations of how to treat the risk (Avoid, Transfer, Mitigate, Accept).
- Delivery of a Risk Register that documents each risk, likelihood, impact, prioritization of each risk.
Security Awareness Training
Employees are a major part of an organization’s attack surface and remain the greatest vulnerability to cybersecurity, frequently targeted by attackers. Ensuring that employees have the knowledge and skills to defend themselves and the organization against threats is an essential part of any security program and a requirement for those organizations that need to comply with government and industry regulations, such as FISMA, PCI, HIPAA or Sarbanes-Oxley. A good security awareness program will educate employees on corporate policies, procedures, standards, guidelines and industry best practices for working with information technology. A critical (yet often overlooked) component of security awareness training is what to do in the event of a data breach. The minutes and hours following the discovery of a data breach are critical to not only preventing the attack from spreading but also to preserving the environment for forensic examination. Our consultants will develop a comprehensive security awareness training program and provide training that is designed specifically for your business.

Our standard approach includes:
- Designing a program that is compliant with the laws and regulations that apply to your business.
- Covering all the basics including physical security, password security, anti-phishing, social engineering.
- Providing training that is role based and includes all roles within the organization
- Diversifying the training content and delivery methods that include instructor lead sessions, self-paced training, simulations, games.
- Making the training intriguing and entertaining.
Information Security Audit
An Information security audit is a structured, systematic and measurable technical assessment of how the organization’s security policy is employed. It is part of the on-going process of defining and maintaining effective security policies. Security audits provide a fair and measurable way to examine how secure an organization is, by performing a security audit your organization can identify and remediate risk before they are compromised. Let our consultants perform a full security audit to uncover weaknesses and security gaps that exist within your organization and uncover the cause of noncompliance to establish an effective security program.

Our standard approach includes:
- Assessing security policies, procedures and controls to determine their operating effectiveness
- Conducting Penetration testing
- Auditing firewall configurations, website code and mobile applications
- Identifying internal control and regulatory deficiencies that could put the organization at risk.
- The delivery of a detail audit report
Endpoint Management
One of the most common and simplest ways a cybercriminal can gain access to your systems and applications is by exploiting known software vulnerabilities on your workstations. There are roughly 30-40 new software vulnerabilities published each day!
While most organizations know their endpoint devices are at risk, many fail to implement adequate security measures due to a lack of time, resources or budget constraints.
Our Endpoint Management Service allows you to outsource all the heavy lifting involved with managing these devices while retaining visibility and transparency across your enterprise.
Our Services Include:
Cybersecurity Vulnerability Management
Vulnerability Management
- Get continuous risk assessment without impacting system or network resources
- Gain insight into the security posture and align the enterprise with the security policies of the organization
- Automatically remediate risks
Patch Management
- Identify and roll out patches automatically
- Keep all major operating systems (Windows, Linux and Mac OS X) as well as third-party applications up-to-date
- Detect and fix configuration deviations, such as password polices and encryption strength
Compliance Management
- Achieve compliance to regulatory standards
- PCI, HIPAA, NIST 800-171, NIST 800-53
- Custom configuration standards
- Fix compliance deviations automatically to ensure that your organization is continuously compliant
Asset Management
- Track software and hardware assets
- Track new installations and changes to configuration settings
- Manage and optimize software licenses and costs
- Blacklist rogue applications that show up in the inventory
Endpoint Management
- Get visibility into the status of endpoint systems, with 100s of built-in checks
- Gather network details and map of devices
- Search for the presence of sensitive data, such as credit card information, soial security numbers, etc.
- Deploy software, block applications and devices
Threat Detection & Response
- Detect Indicators of Attack(IoA) and Indicators of Compromise(IoC)
- Run queries to check for abnormal behavior or unusual network activity that is symptomatic of an attack
- Stop on-going attacks by blocking applications, killing processes, cleaning up startup folders
Legal Technology: Is data privacy a realistic goal?
Download Now
Privacy, Confidentiality, and the Law
Download Now
Data Protection Guide
Download the whitepaper
The Ransomware – How to Prepare and Defend
Download the whitepaper

Discover the Benefits of Managed SOC Services for SMBs
Download the whitepaper
Video Source:
https://www.ftc.gov/tips-advice/business-center/small-businesses/cybersecurity/videos


SMBs, learn how you can begin to build your plan
Download eBook
Our services

Assess & Plan
Educate & Prepare

Monitor & Measure
Information Security Program
Implementing a well-defined and robust security program that is tailored to the specific needs of your business helps to ensure the confidentiality, integrity, availability and privacy of your data and that of your customers. Our advisory services is focused on working with business and technology leaders to develop and implement security programs. Our consultants will develop a comprehensive program and implementation roadmap based on accepted industry best practices and the specific needs of your business.
Our standard approach includes:
- Collecting and analyzing information to understand the goals and objectives of the business, understanding the acceptable risk appetite and tolerance levels of the business.
- Reviewing existing security programs, plans, policies, procedures and controls to determine whether or not security goals and objectives are aligned with those of the business and industry.
- Performing a high-level security assessment to identify the current security posture of the business, high-risk threats and vulnerabilities.
- Working closely with the business and technology leaders to define a security capability maturity level target that is based on the existing capabilities and needs of the business.
- Identifying gaps between the current state capabilities and what is required to achieve the target maturity level.
- Identifying the people, policies, procedures, processes, controls and technologies required to achieve the target maturity level.
- Developing a phased implementation plan and roadmap.

Risk Assessment Services
A critical element in any Information Security Program is how well the organization manages risks. Managing risk involves the identification, assessment, treatment, monitoring and tracking of risk. Since it’s impossible to manage what you don’t know exists, it’s critical to begin any attempt to manage risk by performing a risk assessment to identify, estimate and prioritize the risks to organization’s information assets. To ensure a comprehensive assessment is performed, it’s important to include people, processes and technology in the assessment. Our consultants will develop conduct a Risk Assessment that is tailored to the specific needs of your business and industry.
Our standard approach includes:
- Compiling a list of the information assets of the organization.
- Preforming a business impact analysis to understand the true value of each asset.
- Creating risk scenarios to identify threats and vulnerabilities.
- Combining qualitative and quantitative approaches to estimate the likelihood and potential impact of the risk.
- Providing recommendations of how to treat the risk (Avoid, Transfer, Mitigate, Accept).
- Delivery of a Risk Register that documents each risk, likelihood, impact, prioritization of each risk.

Security Awareness Training
Employees are a major part of an organization’s attack surface and remain the greatest vulnerability to cybersecurity, frequently targeted by attackers. Ensuring that employees have the knowledge and skills to defend themselves and the organization against threats is an essential part of any security program and a requirement for those organizations that need to comply with government and industry regulations, such as FISMA, PCI, HIPAA or Sarbanes-Oxley. A good security awareness program will educate employees on corporate policies, procedures, standards, guidelines and industry best practices for working with information technology. A critical (yet often overlooked) component of security awareness training is what to do in the event of a data breach. The minutes and hours following the discovery of a data breach are critical to not only preventing the attack from spreading but also to preserving the environment for forensic examination. Our consultants will develop a comprehensive security awareness training program and provide training that is designed specifically for your business.
Our standard approach includes:
- Designing a program that is compliant with the laws and regulations that apply to your business.
- Covering all the basics including physical security, password security, anti-phishing, social engineering.
- Providing training that is role based and includes all roles within the organization
- Diversifying the training content and delivery methods that include instructor lead sessions, self-paced training, simulations, games.
- Making the training intriguing and entertaining.

Information Security Audit
An Information security audit is a structured, systematic and measurable technical assessment of how the organization’s security policy is employed. It is part of the on-going process of defining and maintaining effective security policies. Security audits provide a fair and measurable way to examine how secure an organization is, by performing a security audit your organization can identify and remediate risk before they are compromised. Let our consultants perform a full security audit to uncover weaknesses and security gaps that exist within your organization and uncover the cause of noncompliance to establish an effective security program.
Our standard approach includes:
- Assessing security policies, procedures and controls to determine their operating effectiveness
- Conducting Penetration testing
- Auditing firewall configurations, website code and mobile applications
- Identifying internal control and regulatory deficiencies that could put the organization at risk.
- The delivery of a detail audit report

Endpoint Management
One of the most common and simplest ways a cybercriminal can gain access to your systems and applications is by exploiting known software vulnerabilities on your workstations. There are roughly 30-40 new software vulnerabilities published each day!
While most organizations know their endpoint devices are at risk, many fail to implement adequate security measures due to a lack of time, resources or budget constraints.
Our Endpoint Management Service allows you to outsource all the heavy lifting involved with managing these devices while retaining visibility and transparency across your enterprise.
Our Services Include:
Cybersecurity Vulnerability Management
Vulnerability Management
- Get continuous risk assessment without impacting system or network resources
- Gain insight into the security posture and align the enterprise with the security policies of the organization
- Automatically remediate risks
Patch Management
- Identify and roll out patches automatically
- Keep all major operating systems (Windows, Linux and Mac OS X) as well as third-party applications up-to-date
- Detect and fix configuration deviations, such as password polices and encryption strength
Compliance Management
- Achieve compliance to regulatory standards
- PCI, HIPAA, NIST 800-171, NIST 800-53
- Custom configuration standards
- Fix compliance deviations automatically to ensure that your organization is continuously compliant
Asset Management
- Track software and hardware assets
- Track new installations and changes to configuration settings
- Manage and optimize software licenses and costs
- Blacklist rogue applications that show up in the inventory
Endpoint Management
- Get visibility into the status of endpoint systems, with 100s of built-in checks
- Gather network details and map of devices
- Search for the presence of sensitive data, such as credit card information, soial security numbers, etc.
- Deploy software, block applications and devices
Threat Detection & Response
- Detect Indicators of Attack(IoA) and Indicators of Compromise(IoC)
- Run queries to check for abnormal behavior or unusual network activity that is symptomatic of an attack
- Stop on-going attacks by blocking applications, killing processes, cleaning up startup folders

Cybersecurity Maturity Model Certification – CMMC
Subscribe for CMMC Updates
What is the CMMC?
The Office of the Under Secretary of Defense for Acquisition & Sustainment (OUSD(A&S) has been working with DoD stakeholders, University Affiliated Research Centers (UARCs), Federally Funded Research and Development Centers (FFRDC), and industry to develop a new requirement for existing DoD contractors, replacing the current self-attestation model.
The new model released by the Department of Defense (DoD) is the Cybersecurity Maturity Model Certification (CMMC). The intent of the CMMC is to ensure appropriate levels of cybersecurity controls and processes are adequate and in place to protect controlled unclassified information (CUI) on the Defense Industrial Base (DIB).
The DoD is planning to migrate to the new CMMC framework in 2020. The CMMC will serve as a verification mechanism to ensure appropriate levels of cybersecurity practices and processes are in place to protect controlled unclassified information (CUI) that resides on the Department’s industry partners’ networks. CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls. CUI resources, including online training to better understand CUI can be found on National Archives’ website.
The intent of the CMMC is to combine various cybersecurity control standards such as NIST SP 800-171, NIST SP 800-53, ISO 27001, ISO 27032, AIA NAS9933 and others into one unified standard for cybersecurity. In addition to cybersecurity control standards, the CMMC will also measure the maturity of a company’s institutionalization of cybersecurity practices and processes. The CMMC encompasses multiple maturity levels that ranges from “Basic Cybersecurity Hygiene” to “Advanced”.
Why the DoD Created The CMMC
The introduction of the CMMC is the latest step by the Department of Defense (DoD) to mandate that private DoD Contractors adopt cybersecurity standards and practices as part of the government-led effort to protect the U.S. defense supply chain from foreign and domestic cyber threats, and reduce the overall security risk of the sector.
Highlights of the CMMC
- A single standard used across all DoD contracts starting in 2020-2021
- The required CMMC level will be contained in RFP sections L & M starting midyear 2020
- All DoD Contractors will need to become CMMC Certified by passing a CMMC Audit to verify they have met the appropriate level of cybersecurity for their business. This will be a “go/no-go” requirement for any organization who wants to hold contracts with the Department of Defense.
- Self-certification is not allowed. A certified independent 3rd party organization will conduct the audit.
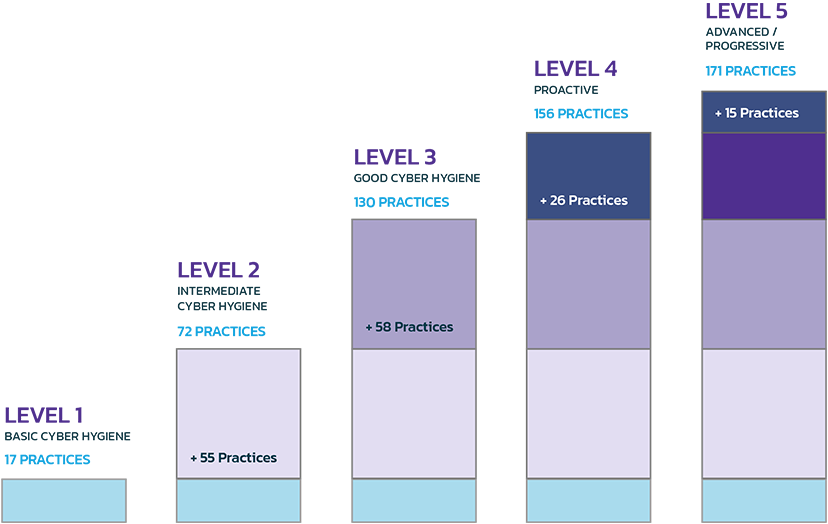
- The CMMC consists of 5 levels from basic hygiene (Level 1) to advanced (Level 5). Most RFPs are expected to require a Level 1 to Level 3 certification.
- The certification cost has not yet been determined. The cost, and associated assessment will likely scale with the level requested.
- The goal is for CMMC to be cost-effective and affordable for small businesses to implement at the lower CMMC levels.
Summary of CMMC Levels

CMMC Domains
The CMMC model consists of 17 domains. The majority of these CMMC domains originated from the Federal Information Processing Standard (FIPS) and the NIST SP 800-171.

Practice Levels

Practices
What you need to know
Even if your organization does not handle Controlled Unclassified Information (CUI), all companies conducting business with the DoD must be certified. The level of certification required will depend upon the amount of CUI a company handles or processes.
- The government will determine the appropriate tier of certification for the contracts they administer. The required CMMC level will be contained in sections L & M of the Request for Proposals (RFP).
- All DoD Contractors will need to become CMMC Certified by passing a CMMC Audit to verify they have met the appropriate level of cybersecurity for their business.
- There is no self-certification. Certifications will only be credited through CMMC Audits.
- Your company will coordinate directly with an accredited and independent third-party commercial certification organization to perform the CMMC assessment. Your company will specify the level of the certification requested based on your company’s specific business requirements.
- Certification will be awarded at the appropriate CMMC level upon demonstrating the appropriate maturity in capabilities and organizational maturity to the satisfaction of the assessor and certifier.
- The certification cost has not yet been determined. The cost and associated assessment will likely scale with the level requested. The cost of certification will be considered an allowable, reimbursable cost and will not be prohibitive.
- Your certification level will be made public; however, details regarding specific findings will not be publicly accessible. The DoD will see your certification level.
- The duration of a certification is still under consideration.
- If your company is certified and your company is compromised, you will not lose your certification. However, depending on the circumstances of the compromise and the direction of the government program manager, you may be required to be recertified.
- Engage a partner like PamTen to assist with pre-certification readiness. We’ll partner with you to determine your high-level maturity level, establish hygiene best practices, and implement a cybersecurity program to prepare your organization. Contact us now to learn how PamTen can help.
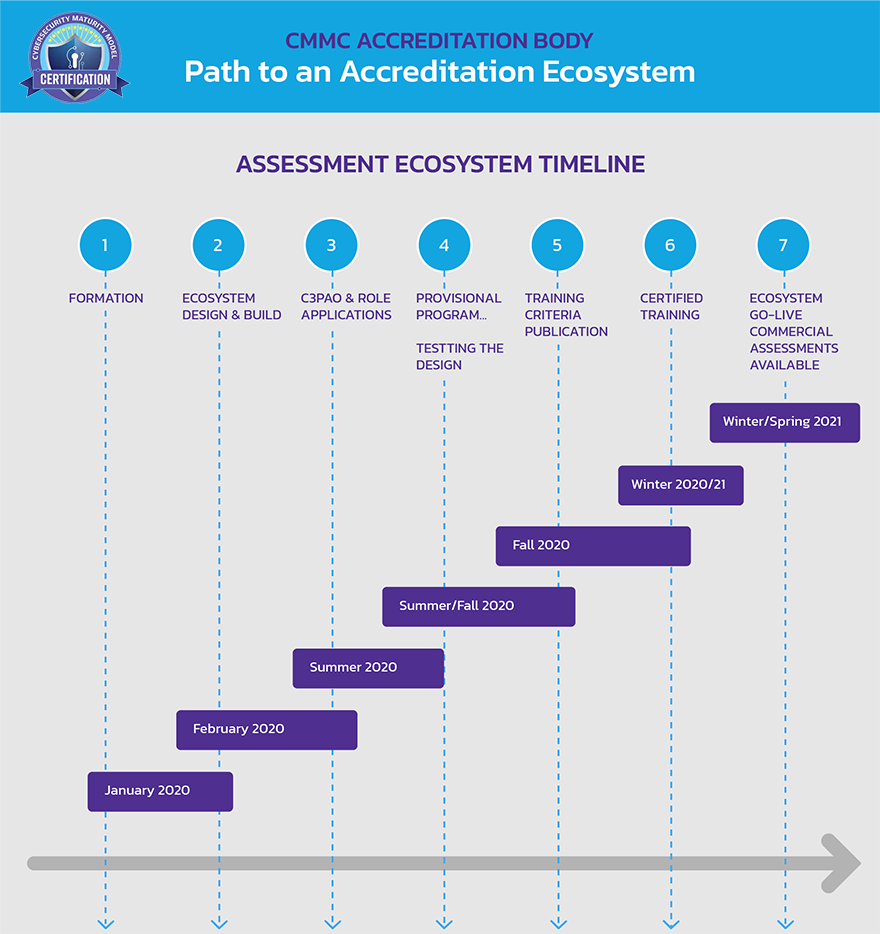
Important Dates
Version 0.7 of the CMMC framework was released on December 6th, 2019. This version includes CMMC Levels 1-5 as well as the associated discussion and clarification for a subset of practices and processes. In June 2020, industry should begin to see the CMMC requirements as part of Requests for Information. The initial implementation of the CMMC will only be within the DoD.
- Winter/Sprint 2020/2021 – EcoSystem Go Live
- Winter 2020/2021 – Certified Training
- Fall 2020 – Training Criteria Published
- September 2, 2020 – CMMC-AB Approves First 11 Licensed Partner Publishers (LPPs) to Deliver Certification Curriculum
- August 31, 2020 – CMMC-AB announced that it has signed an MOU with Dun & Bradstreet to provide, as a partner, financial and ownership background checks for the organizations applying for accreditation by the CMMC-AB.
- January 30, 2020 – CMMC Model v1.0 released
- January 27, 2020 – CMMC Accrediting Body Board of Directors announced
- December 6, 2019 – CMMC version v0.7 released
- December 4, 2019 – Accreditation Body follow-up meeting held
- November 19, 2019 – Accreditation Body kickoff meeting held
- November 8, 2019 – CMMC version v0.6 released
- October 10, 2019 – CMMC Accreditation Body RFI
- September 5, 2019 – CMMC version v0.4 released
References
- Understanding CUI – https://www.archives.gov/cui/training.html
- Securing Defense – Critical Supply Chains https://www.ndia.org/-/media/sites/policy-issues/cmmc-brief—5-jun-19.ashx?la=en
- CMMC website – https://dodcio.defense.gov/CMMC/
- CMMC FAQs – https://dodcio.defense.gov/CMMC/FAQ/
- The Cybersecurity Maturity Model Certification Accreditation Body (CMMC-AB) website – https://dodcio.defense.gov/CMMC/
- Download CMMC version v2.0 – https://dodcio.defense.gov/CMMC/
Contacting Us
https://www.pamten.com/
500 College Road East, Suite 234,
Princeton, NJ – 08540, USA
609-212-0524
cybersecurity@pamten.com
Cybersecurity Resources
Cybersecurity Free Resources
Free Resources
https://staysafeonline.org/programs/cybersecure-my-business/
– National Cyber Security Alliance program helping small and medium-sized businesses (SMBs) learn to be safer and more secure online.
https://www.ftc.gov/tips-advice/business-center/small-businesses
– Federal Trade Commission guide and resources for protecting small businesses.
https://www.nist.gov/itl/smallbusinesscyber
– National Institute of Standards and Technology (NIST) The small business cybersecurity corner provides free information produced by federal agencies, including NIST and several primary contributors, as well non-profit organizations and several for-profit companies.
https://www.cisa.gov/cyber-guidance-small-businesses
– Federal Department of Homeland Security (DHS) guides and links to resources for small business including best practices and technical guidance.
– List of websites and whether they support 2FA.
– NJ Cybersecurity and Communications Integration Cell (NJCCIC) is the State’s one-stop shop for cybersecurity information sharing, threat analysis, and incident reporting.
– FBI’s service organization for partnership between private sector and FBI in promoting awareness and best practices against cybercrime. Open to businesses and individuals.
https://www.cisecurity.org/cybersecurity-tools/
– Center for Internet Security, Inc. is a non-profit entity that harnesses the power of a global IT community to safeguard private and public organizations against cyber threats.
Training
https://register.graduateschool.edu/modules/shop/index.html?action=courseBrowse&CatalogID=57
– The Federal Virtual Training Environment (FedVTE) provides free courses without login requirements.
https://www.fbi.gov/investigate/cyber
– FBI overview for areas of cybercrime with resources for training of all ages in best practices.
– Cybrary provides thousands of free online Cyber Security training classes.
https://www.sans.org/security-awareness-training/resources
SANS free security awareness posters, videos, and resources
– Try Hack Me provides hands on learning paths in multiple areas of cybersecurity. Includes intro courses for those with no experience in cybersecurity as well as advanced techniques for experienced learners.
– Pluralsight provides in-depth learning paths for specific topics
https://www.linkedin.com/learning
– LinkedIn Learning provides expert-led courses across a variety of online class topics for every step of your career.
https://www.eccouncil.org/train-certify/
– The EC-Council offers training and certification programs
https://www.isc2.org/certifications/cc
– The International Information System Security Certification Consortium provides training and certification programs.
Formal Education
https://www.usnews.com/best-colleges/rankings/computer-science/cybersecurity
– Best Undergraduate Cybersecurity Programs
https://fortune.com/education/information-technology/best-masters-in-cybersecurity/
– Best Master’s in Cybersecurity Degrees in 2023
– 50 Best universities for cybersecurity and information assurance.
IT Security Frameworks
NIST
https://www.nist.gov/cyberframework/framework
– Framework documents
https://www.nist.gov/cyberframework/new-framework
– For those who are new to the framework
ISO
https://www.iso.org/standard/73906.html
– ISO/IEC 27001
https://www.iso.org/standard/27001
– ISO/IEC 27001
https://www.iso.org/standard/54533.html
– ISO/IEC 27002
https://www.cisecurity.org/controls/
– CIS Critical Security Controls
https://complianceforge.com/grc/nist-800-53-vs-iso-27002-vs-nist-csf-vs-scf
– Comparison of the most widely used frameworks
IT Security Policies
https://resources.infosecinstitute.com/topic/key-elements-information-security-policy/
– Key elements of an information security policy
https://www.sans.org/reading-room/whitepapers/policyissues/paper/509
– Building and implementing a security policy
– An Incremental Approach to Building an Information Security Program
Security Policy Templates
https://www.sans.org/information-security-policy/
– SANS Security Policy Templates
https://www.healthit.gov/topic/privacy-security-and-hipaa/privacy-security-resources-tools
– Information Security Policy Template
– Information security policies from a variety of higher education institutions
Incident Reporting
– List of federal agencies that investigate computer hacking, fraud and other internet-related crime
https://www.ic3.gov/Home/Index
– FBI Internet Crime Compliant Center (IC3) accepts online Internet crime complaints from either the actual victim or from a third party to the complainant.
– FraudSupport.org is a program created by the Cybercrime Support Network to provide assistance to both individual and small business cybercrime victims. FraudSupport.org will lead cybercrime victims through the Report, Recover and Reinforce process after an incident occurs.
– Federal Trade Commission guide with steps to take once a breach has occurred
Please subscribe for the latest updates SUBSCRIBE
Please register to our Cybersecurity Community Register