
5G networks will usher in a wave of new IoT (Internet of Things) applications. As with the implementation of any new technology, it is vital to ensure that a secure foundation is in place. This is especially important when we consider that 5G will accelerate the deployment of smart devices and the applications they support. Tech analyst company IDC predicts that by 2025 there will be 41.6 billion connected IoT devices, generating 79.4 zettabytes (ZB) of data.
Mobile network security vulnerabilities are not new, and they will not go away with 5G. Overall, 5G is more secure than 4G. Many industry experts have warned of the 5G security gaps and vulnerabilities. A 2019 Brooking report identified five ways in which 5G networks are more vulnerable to cyberattacks than their predecessors, and Purdue University and the University of Iowa researchers identified 11 new vulnerabilities in 5G.
As 5G becomes widely available, the deployment of IoT devices and applications will increase. Each IoT device connected to the network becomes a new entry point of attack that can be exploited. If an attacker can successfully gain access to the IoT device, they can attack other devices on the network. Considering that some IoT devices access and control environmental systems and critical infrastructure, there are significant life and safety risks if these systems are compromised.
While the network providers are responsible for securing the 5G network, the end-user plays a critical role in securing the devices they connect to their network. We know that many organizations struggle with implementing simple cybersecurity best practices.
What are the additional security challenges these organizations face when 5G is widely available fueling the acceleration of IoT? Are their security teams equipped with the knowledge, skills, and tools necessary to manage IoT?
To help organizations manage IoT cybersecurity and privacy risk, the NIST has published the Considerations for Managing Internet of Things (IoT) Cybersecurity and Privacy Risks. The NISTIR 8228 provides a framework and set of recommended actions to address the risks associated with IoT devices.
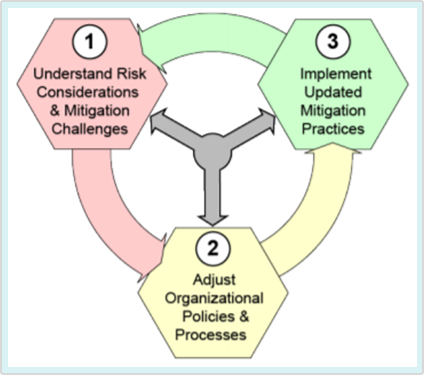
The NIST IoT framework provides a starting point for addressing IoT risk. The framework stresses the importance of identifying and addressing the cybersecurity and privacy risk considerations and challenges throughout the IoT device lifecycle and includes:
Following the NIST IoT framework and implementing IoT best practices such as the ones listed below can help your organization limit your security exposure and develop a comprehensive IoT security program.
Preparing for IoT risk now will enable your organization to take advantage of the opportunities presented by IoT to transform and grow the business.
For more information, please email John Mendes at john.mendes@pamten.com.