
If you are wondering whether or not you need a Cyber Security Risk Assessment, you probably need one.

What is a Cyber Security Risk Assessment?
A Cyber Security Risk Assessment is a comparison of the overall strength of your organization’s cyber security program that includes your approach to risk management and oversight, policies, controls, incident response management, etc. against a standard information security framework.
Purpose of Cyber Security Risk Assessment
The purpose of the risk assessment is to systematically identify and assess cyber security risk to the organization’s strategy, operations, brand, reputation, assets, and resources.
The path to improving your cyber security program begins by first determining your current strengths and vulnerabilities.
An effective risk assessment will:
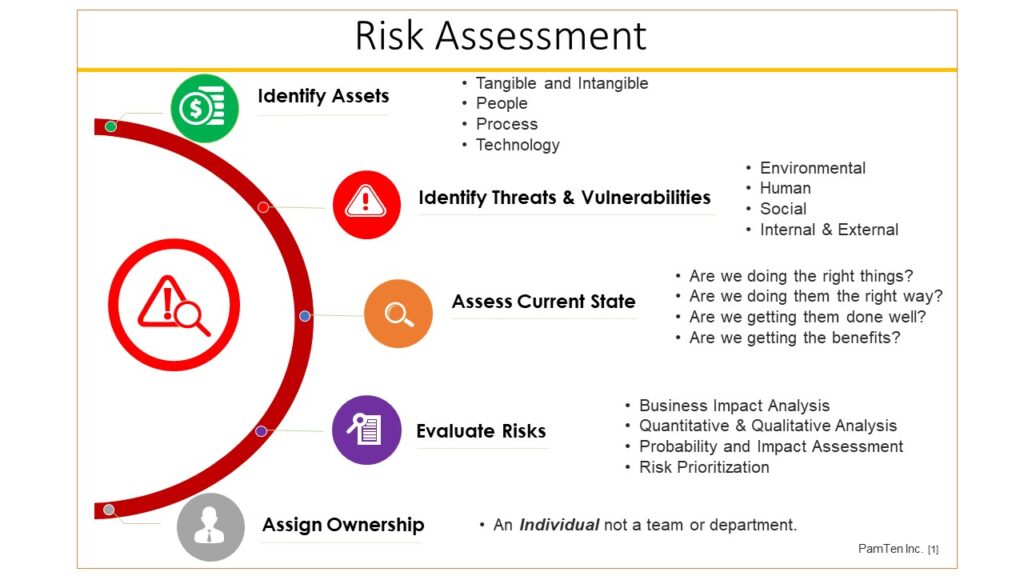
Information Security Frameworks
An information security framework is a series of documented processes used to define policies and procedures around the implementation and ongoing management of information security controls. Another way to think about security frameworks is that they describe “what” an organization will do to manage security risks. These frameworks are a blueprint for building an information security program to manage risk and reduce vulnerabilities.
Some frameworks were developed for specific industries or to satisfy individual regulatory compliance goals. Frameworks are often customized to solve particular information security problems. Frameworks vary significantly in complexity and scale, with some requiring extensive documentation, long implementation timelines, and large budgets to obtain and maintain certification.
There is a large amount of overlap among many of these frameworks in terms of general security concepts. These overlaps allow “crosswalks” to be built between frameworks to show compliance across frameworks.
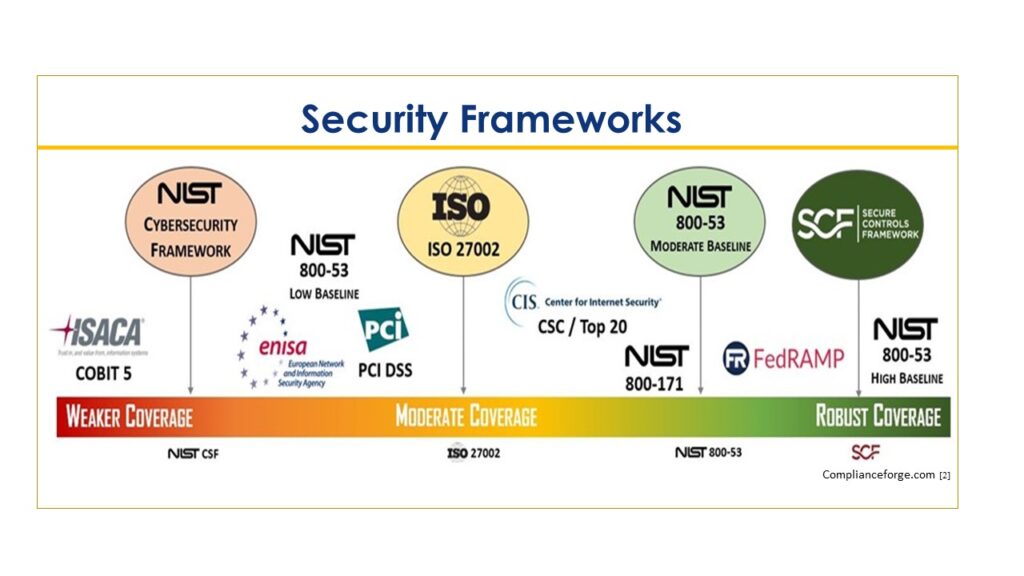
Selecting an Information Security Framework
Given the confusing array of information security frameworks, it’s understandable why many organizations have either not chosen a framework or have developed an ad hoc framework. Gartner research shows that 21% of clients had not selected a security framework.
Selecting a security framework doesn’t have to be a complicated and or time-consuming process. Any of the major information security frameworks will help you organize and manage your information security program. When selecting a framework, keep in mind the unique needs of your industry, regulatory compliance requirements, customer expectations, and the IT and security capabilities of your organization. Selecting a framework that is over-kill for your organization or one that doesn’t address your specific industry or regulatory compliance requirements can result in gaps, wasted time, and money and overload your team with much more than what they can handle.
The decision to use a particular framework is driven by multiple factors, including industry type and compliance requirements. Publicly traded companies may select ISACA’s COBIT[4] framework, given its focus on integrating IT with accounting and financial systems, making it easier to comply with Sarbanes-Oxley. The ISO 27000 [5] series was developed by the International Standards Organization. It provides a broad information security framework that can be applied to businesses of all types and sizes. It can be thought of as the information security equivalent of ISO 9000 quality standards for manufacturing. It is best used when a company needs to market information security capabilities through the ISO 27000 certification. NIST SP 800-53 [6] is the standard required by U.S. federal agencies but can also be used by any company to build a technology-specific information security program.
Why perform a Cyber Security Risk Assessment?
While you cannot control threats or eliminate all vulnerabilities, you can manage your organization’s readiness to respond by understanding your environment, proper planning, strong policies, adequate controls, and training your staff. By evaluating the likelihood and impact of an attack, you are better equipped to ensure that the executive level and functional management are aligned on security risks and priorities.
Key reasons for conducting a Cyber security Risk Assessment:
It’s impossible to eliminate all threats and vulnerabilities. Stop focusing on the high-profile threats you hear about in the media and resist the temptation to buy the latest and greatest product claiming to be the cure-all solution and start building an effective Cyber security program. A cyber security risk assessment will arm your leadership team with the knowledge required to build a solid foundation to improve your overall security posture.
Sources:
Schedule a conversation with one of our experts.
Not ready to speak with us, that’s fine. Try-out our Risk Assessment Tool at no cost or obligation.
FREE RISK ASSESSMENT